Top Notch Tips About How To Detect Hardware Keyloggers

Another classic option is to use an antivirus to detect threats.
How to detect hardware keyloggers. Malwarebytes can detect applications that can harvest keystrokes and it can create a smooth path for the hackers to get critical information. Press win + i at the same time to open windows. Here, you can see which processes are running.
The truth is, keyloggers are not easy to detect without the help of security software. Someone used your login credentials to gain unauthorized access to another site. As manual detection is hard to follow through, we will start with the.
Up to 30% cash back use the task manager. Trend micro housecall is an online. Like most malware, you can use a good antivirus/anti.
It can detect and can store the actual keystrokes entered by the user/victim. The simplest way to detect a keylogger is to check your task manager. The answer is, it depends.
Open malwarebytes > click on the update tab across the top> get the latest updates. So, always check for additional. Turn off auto detecting of hardware.
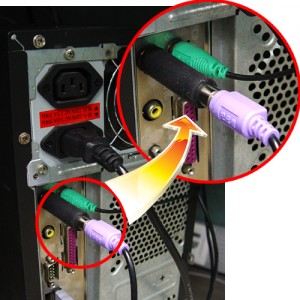
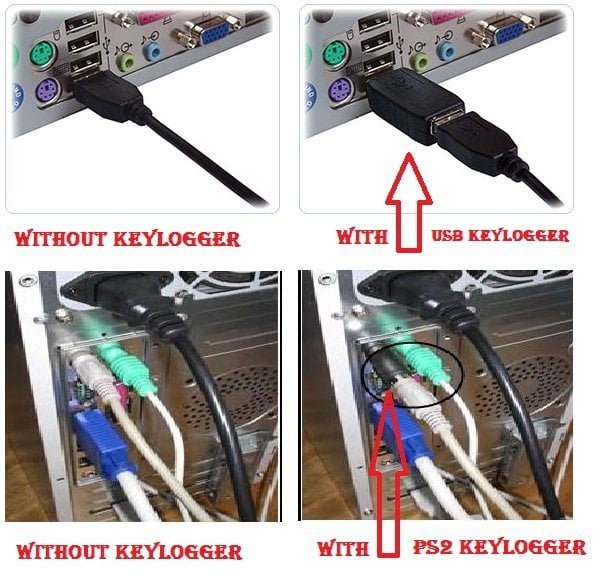
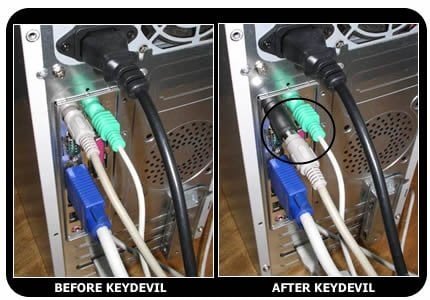
Use a public or borrowed computer 2. It can be tough to know which ones are legitimate and which could be. For hardware keylogger one must have physical access.